Stop Using Passwords Now.
Very few things on the internet have survived in their original form since its conception. Passwords are one of them.
Nobody likes passwords. We have learned to tolerate them as a ‘necessary inconvenience’ of the digital age and having to remember, type, forget or share our passwords with people is a price to pay for online security. But it shouldn’t necessarily be that way.
After nearly 30 years of existence in mainstream digital culture, research data and human experience demonstrate how badly passwords perform as a design solution. From a purely human usability perspective, passwords have become a frustrating, ineffective and unsophisticated method for accessing and protecting digital space. It’s time to free people from this burden. This is why:
1. Too many passwords in our lives

Passwords (like phone numbers) were a practical idea when you had to remember a few of them. Today, a personal email address is associated with an average of 130 accounts, not to mention offline objects for which we have to remember secret codes (from devices and credit cards to digital door locks). These numbers have been growing as the internet, and technology in general, have become ever more present in our lives.
As with phone numbers, we quickly reached the point where it is impossible to manage this amount of information without the need for external help. Hence browsers than remember your passwords for you, the “remember me” and ‘I forgot my password” buttons and Password Managers. The very existence of the Password Manager market is a symptom of the problem while also being a solution for it. But the idea of storing all of your passwords in one basket protected by… a password (and having to pay for an app to remember things for you) is absurd. The question that needs to be asked is: do we really need so many passwords?

The human response to the problem of having hundreds of accounts is to use the same password for everything even though it goes against security best practices and guidelines. In fact, according to a survey by PasswordBoss, a staggering 59% of users reuse the same password. When companies became aware of this problem, they started imposing password strength constraints, forcing people to deal with multiple passwords, which takes us to the next problem.
2. People can’t come up with good passwords
Back in 2007, a large scale study by Microsoft on web password habits simply concluded that people have weak passwords and that they forget them, both of which are problems related to human cognitive abilities and not to technology.
An analysis by the UK’s National Cyber Security Centre (NCSC) on breached accounts found that “123456” and “123456789” were the most widely-used password while others in the top five included “qwerty”, “password” and 1111111. Obviously, these passwords are easily guessable by low-tech algorithms and hackers don’t need to make much effort to break into the majority of accounts. You can take a look at the list of breached passwords for yourself.
Coming up with strong passwords is not an easy task, considering that passwords are usually defined while the user is trying to do something else, like signing up to make a payment. This explains why people prefer to go with their usual, familiar passwords instead of making the effort of coming up with strong ones. Password managers allow users to create completely random and meaningless passwords and remember them for you; the price (and the strategy) is user dependence on the tool and losing control over your passwords. You have little choice anyway.
As the extensive PEW report on internet security found out, just 7% of people use Password Managers. For everyone else, password strength constraints have proven ineffective as hacking techniques become more sophisticated and outperform human imagination in coming up with enigmatic strings of characters. Making passwords complicated and hard to remember doesn’t work for people, which is why the National Institute of Standards and Technology (NIST) now recommends that complexity requirements and periodic password changes no longer be forced on users.
3. People manage passwords badly
As Don Norman explains in his work (Living with Complexity, The Design of Everyday Things) one common solution for dealing with the limits of human memory is to put information in the world to use the world as information when we need it. This is especially applied to information that is needed in precise contexts, like road signs, exit signs, sticky notes, to-do lists, instructions on products, manuals, etc.
Putting your password in the world is the antithesis of security; nevertheless, according to this PEW report, against all security rational, 49% of American users write down their passwords to keep track of them. One-quarter (24%) of online adults keep track of their passwords in a digital note or document on one of their devices.
This is not human carelessness but rather a sign that a solution has become a problem for users.
4. Passwords are anachronistic for today’s digital habits
If we look at how people use the internet today (considering desktop and mobile usage patterns), it seems that password-protected authentication is stuck in the 90s:
Passwords were also useful when most people accessed the internet from public spaces and shared computers at home. In those situations, logging in and out was a frequent and acceptable task. Today, most usage is on personal devices that are or can be protected by passwords.
- Mobile usage has surpassed desktop usage since 2016. In real life, once the user as unblocked their mobile device, they have access to apps and functions without the need for additional in-app authentication. Smartphones basically perform as password managers. Some apps even keep you authenticated even after you delete them.
- Very few online services are used regularly: A study found that on smartphones, people use only 5 apps regularly. On desktop computers, people usually stay signed in on the websites they use regularly. Authentication happens in rare cases like when one uses a different device, changes browsers or deliberately logs out of a service.
- Most online services are used infrequently and user accounts are dormant. You are usually asked to insert your password for these services but since you use them rarely, you tend to forget them.
All this means that people engage in the authentication process at a decreasing rate. In other words, we are typing our passwords less often, giving us fewer reasons to remember them.
Alternative solutions
We cannot get rid of passwords completely in the near future because of the scale of their usage and the technical effort needed to make the transition to alternative solutions. I doubt that user habit and adoption might be an issue because nobody will miss their passwords if a better solution is offered instead.
Here are 4 alternatives:
1. Email login
Email login is probably the easiest and most efficient alternative to passwords (and surprisingly underused). It replaces passwords by using a time-limited token sent by email to the user. Everybody has an email account and we rarely change or delete it. Email is already used as the middleman to confirm signup, recover forgotten passwords and for extra security steps. Why not just make it the default login method?
Email login is universally applicable and requires no special technology, but it is especially suitable for services that are used infrequently (which are, as explained above, the majority of services). In practice, it delegates security to the user’s email service.
Medium was one of the first websites that introduced password-free login in 2015 but few major companies have followed that path. Amazon uses single-use sign-in codes sent to users when they have difficulty accessing their account.
2. Single Sign-on (SSO)
SSO is another way of getting rid of multiple passwords within a fragmented and disparate ecosystem by enabling users to access multiple services using a single account (the same way a Google account or Apple ID give users access to all services on their respective platforms). If combined with email login, it can solve the problem of having multiple accounts and passwords at the same time.
SSO is widely implemented in companies but it is also possible to use it for non-professional use: the French government has implemented a mechanism called ‘France Connect’ which allows french residents to access almost all government services with their social security number and a single password. (Note that the government cannot suppose that every user has an email address so email login cannot be forced.)
Third-party authentication (also known as social login) is similar to SSO by using data from another account in order to give access to a service. But some users might be reluctant to use this option for privacy issues regarding third-parties gaining access to their data, as once happened with Facebook. The choice of eligible parties is also limited and not everyone uses the accounts allowing this functionality. Another problem with this method is that the user becomes dependent on the third-party account: should they wish to delete it, they might lose access and data associated with other services.
3. Physiological Biometrics: Fingerprint, Face Recognition, Voice
Biometrics have gained a lot of attention and popularity in the last few years in mobile devices, but their application in web interfaces and software lags behind.
Apple first put Touch ID on the iPhone 5s in 2013; since then, many other tech giants have followed suit. Today, they’re basically a given feature on flagship smartphones. Face Recognition is rising in popularity thanks to the proliferation of cameras in digital devices and selfie culture. Apple boldly replaced Touch ID with Face ID since iPhone X. In 2017, Master Card rolled out “selfie payments” in Europe, a feature that identifies a user by face recognition in order to authorize payments. Other companies experiment with voice. In 2016, several banks such as HSBC and Barclay’s introduced voice recognition technology to identify their customers.
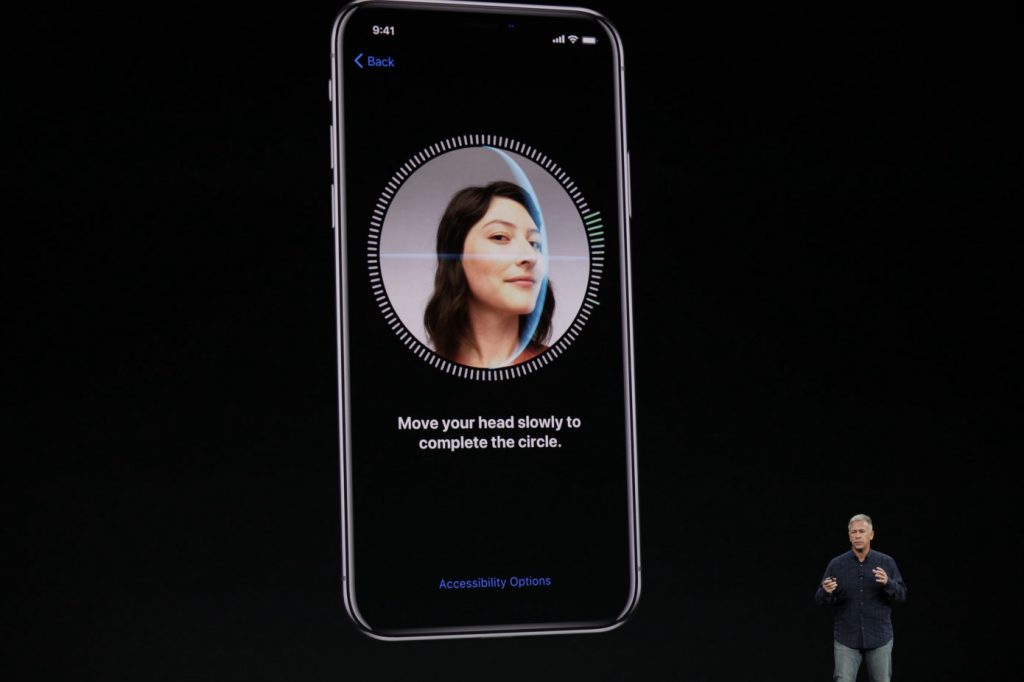
Biometrics rely on hardware capabilities and are a good choice for systems that are accessed through specific devices but fallback methods should be provided in case the user does not have access to the appropriate hardware.
Biometrics might easy to use but they have a fundamental flaw compared to passwords: if you’re captured by criminals or taken into the custody of law enforcement, they can unlock your phone by holding it up to your face. Technology is not yet smart enough to understand the difference between a real unlock attempt and a forced one and I doubt that there is a solution for it. Apple has recognized this flaw and has made it possible to disable Face ID and Touch ID.
4. Physical keys
For high-risk operations, high-security environments or sensitive users (like system administrators) we can use physical security keys such as Google’s Titan or Yubiko’s YubiKeys. Today, security keys are mostly used for 2-factor authentication in combination with passwords but technically they can replace them.

Accessibility
Most of the research and data used in this article were done on American users and my analysis applies to technologically-advanced contexts. There are still places in the world where people use the internet through public internet cafés, schools, universities and public libraries. Not everyone has a personal laptop and some families might share one computer. Most people in the world cannot afford expensive smartphones with the latest generation of fingerprint readers. Considering these situations, I believe email login is the best alternative to passwords for daily, non-critical usage.
Conclusion
People are bad at creating strong passwords, forget them and are coming up with desperate solutions for managing the unmanageable while the concept of passwords itself is becoming increasingly irrelevant in today’s technological context.
I am not suggesting that we should create a password-free world but I believe we should limit their usage; passwords are necessary in a few cases, for example when the access key to a system should only be stored in the user’s mind. But for ordinary, uncritical every-day use, this is not the case. Instead of making passwords the default way of protecting user accounts, we can easily replace them with better, already existing solutions without compromising security. Life is too short to spend it on trying to remember if you used an S or a $ in «mYd0g$!3d!».
This article was originally published on UX Planet

